| Boing Boing ( @ 2013-03-26 20:05:00 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Ars Technica's Nate Anderson decided to try cracking passwords (from a leaked file of MD5 hashes), to see how difficult it was. After a very long false start (he forgot to decompress the word-list file) that's covered in a little too much detail, Anderson settles down to cracking hashes in earnest, and provides some good data on the nuts and bolts of password security:
By this point I had puzzled out how Hashcat worked, so I dumped the GUI and switched back to the command-line version running on my much faster MacBook Air. My goal was to figure out how many hashes I could crack in, say, under 30 minutes, as well as which attacks were most efficient. I began again on my 17,000-hash file, this time having Hashcat remove each hash from the file once it was cracked. This way I knew exactly how many hashes each attack solved.
This set of attacks brought the number of uncracked MD5 hashes down from 17,000 to 8,790, but clearly the best "bang for the buck" came from running the RockYou list with the best64.rule iterations. In just 90 seconds, this attack would uncover 45 percent of the hashed passwords; additional attacks did little more, even those that took 16 minutes to run.
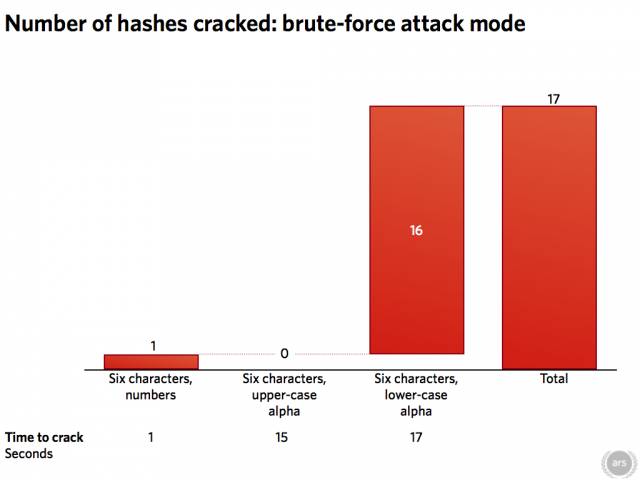
Cracking a significant number of the remaining passwords would take some much more serious effort. Applying the complex d3ad0ne.rule file to the massive RockYou dictionary, for instance, would require more than two hours of fan-spinning number-crunching. And brute force attacks using 6-character passwords only picked up a few additional results.
The point, really, is that if you want to understand the relative security of different password-generation techniques, you need to understand what's involved in state-of-the-art password cracking techniques.
How I became a password cracker ![]()


